- 12 Oct 2023
- 3 Minutes to read
- Print
- DarkLight
Managing User Roles and Permissions
- Updated on 12 Oct 2023
- 3 Minutes to read
- Print
- DarkLight
Secure Edge Portal users can perform sets of operations based on the role assigned to them.
By default, two roles are available: Admin and Read Only. Table 2 lists some of the operations that define default and custom roles for performing various functions in the Secure Edge Portal.
Table 2. Roles and Associated User Operations
| Component | Admin | Read Only |
|---|---|---|
| Network | Add/delete network View/edit network Connect/disconnect network | View network |
| iNode | Add/delete iNode Edit iNode Collect diagnostic data | View iNode details |
| Org | Create child org Create user and roles | View org details |
| Role | Add/view roles | View roles |
| Service | Install services Delete services View service logs | View service |
| User | View/edit user Add/delete user | View list of all users |
Table 3 lists the default roles and their associated permission names.
Table 3. Default Roles and Associated Permissions
| Default role | Permissions |
|---|---|
| Read Only | NODE:READ, NETWORK:READ, SERVICE:READ, ORG:READ, USER:READ, ROLE:READ |
| Admin | NODE:ADMIN, NODE:READ, NODE:REBOOT, NETWORK:READ, NETWORK:ADMIN, NETWORK:CONNECT_DISCONNECT, NETWORK:DIAGNOSTIC, SERVICE:ADMIN, SERVICE:READ, ORG:ADMIN, ORG:READ, USER:ADMIN, USER:READ, ROLE:ADMIN, ROLE:READ, PKI:ADMIN, EVENT:DOWNLOAD, EVENT:VIEW, ACTIVITY:DOWNLOAD, ACTIVITY:VIEW |
Table 4 lists and describes all the available permissions. On the Roles page, in the Permissions field,
you can hover over a permission name to display a description of its access level(s).
Table 4. Available Permissions
| Permission | Description |
|---|---|
| NODE:READ | Allows read access to all clusters, nodes, networks, services, service template, profiles (config template), techdump, ssh public keys, PKI, iNode and service statistics view, iNode upgrade history and container image under the respective namespace, node cli, monitoring, and duplicate address detection (DAD). |
| NODE:ADMIN | Allows administrator access to all nodes, networks, services, service template, profiles (config template), techdump, iNode upgrade history and container image, and iNode and service statistics view. Also allows read access to PKI under the respective namespace, cluster management, node cli, monitoring, DAD, and representation network automation. |
| NODE:REBOOT | Allows reboot and iNode service statistics view access to all nodes under the respective namespace. |
| NETWORK:READ | Allows read access to all networks and vinet under the respective namespace. |
| NETWORK:ADMIN | Allows administrator access to all networks and vinet under the respective namespace. |
| NETWORK:CONNECT_DISCONNECT | Allows connect and disconnect access to all networks under the respective namespace. |
| NETWORK:DIAGNOSTIC | Allows read access to all nodes’ techdump under the respective namespace. |
| SERVICE:READ | Allows read access to all services and secrets under the respective namespace. |
| SERVICE:ADMIN | Allows administrator access to all services and secrets under the respective namespace. |
| ORG:READ | Allows read access to organization, user, role, ssh public keys, and permission(s). |
| ORG:ADMIN | Allows access to the following functions: create a new organization, user, and role; create/update organization policy, reset twofactor authentication (2FA), initiate verify email, assign certificates to organization under the respective namespace, manage public keys, manage ssh access on iNodes and administrator access to apikey, access events at organization and node level, and access notification channels. |
| USER:READ | Allows read access to users’ roles under the respective namespace. |
| USER:ADMIN | Allows administrator access to users and roles, initiate verify user email, and create/get apikey under the respective namespace. |
| ROLE:READ | Allows read access to roles under the respective namespace. |
| ROLE:ADMIN | Allows administrator access to roles under the respective namespace. |
| PKI:ADMIN | Allows administrator access to PKI (public key infrastructure). |
| EVENT:DOWNLOAD | Allows access to download event logs. |
| EVENT:VIEW | Allows access to view organization and node level events. |
| ACTIVITY:DOWNLOAD | Allows access to download activity logs. |
| ACTIVITY:VIEW | Allows access to view activity logs |
Creating User-defined Roles
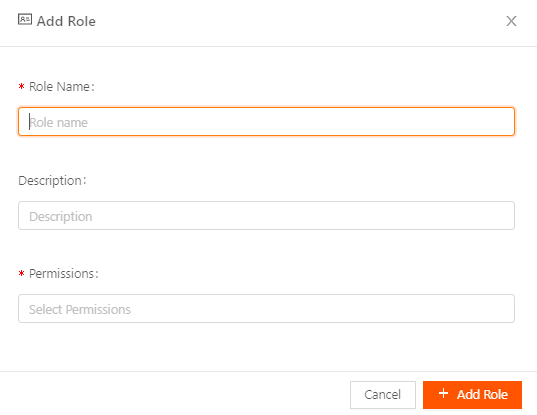
To create user-defined roles, follow these steps:
- Login to Secure Edge Portal with an Admin user role.
- From the left menu, select Users > All Roles.
- In the top right, select the plus sign icon (+) to add a new role.
- Enter the Role name, a Description, and select the Permissions from the list.
- Click + Add Role.
Assigning a User-defined Role
To assign a user-defined role, you create a user account for the user and map a role to that user. Follow these steps:
- To add a user, at the top of the Orchestrator left menu select the plus sign icon (+) > Add User.
- Enter the user details and select the role to assign this user.
- Click Add User.
- To confirm the role has the permissions you intended, log in as the user and confirm the appropriate operations are available.
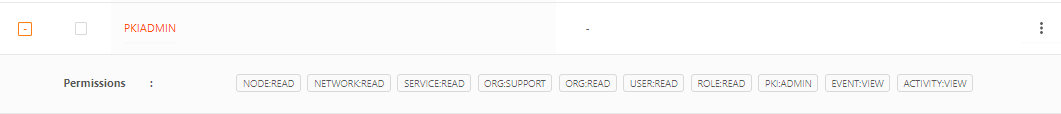
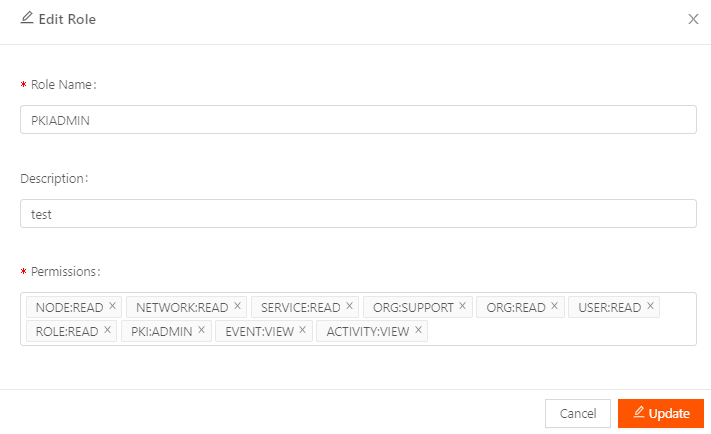
Viewing/Editing Roles
The administrator can view the list of roles and view/edit the permissions applied to a role. Default roles cannot be edited.
- On the Orchestrator left menu, select Users > All Roles to view the current roles and their set permissions.
- On the Roles page, in the left column, click the + to expand the current permissions for a specific role. Or click the role name to view its description and permissions.
- To view or edit the role, click the View/Edit icons on the menu (vertical dots) to the far right.
- Modify the desired fields. You can hover over a permission to display a short description.
- Click Update.