- 26 Aug 2024
- 14 Minutes to read
- Print
- DarkLight
Provision and Launch Virtual iNodes and Virtual Edge iNodes with Azure
- Updated on 26 Aug 2024
- 14 Minutes to read
- Print
- DarkLight
This article describes how to provision and launch Virtual iNodes and Virtual Edge iNodes on Azure.
Provisioning and Launching Virtual iNodes on Azure
In this section, learn how to provision and launch a Virtual iNode on Azure.
Provision a Virtual iNode on Azure
To provision a Virtual iNode with Azure, follow these steps:
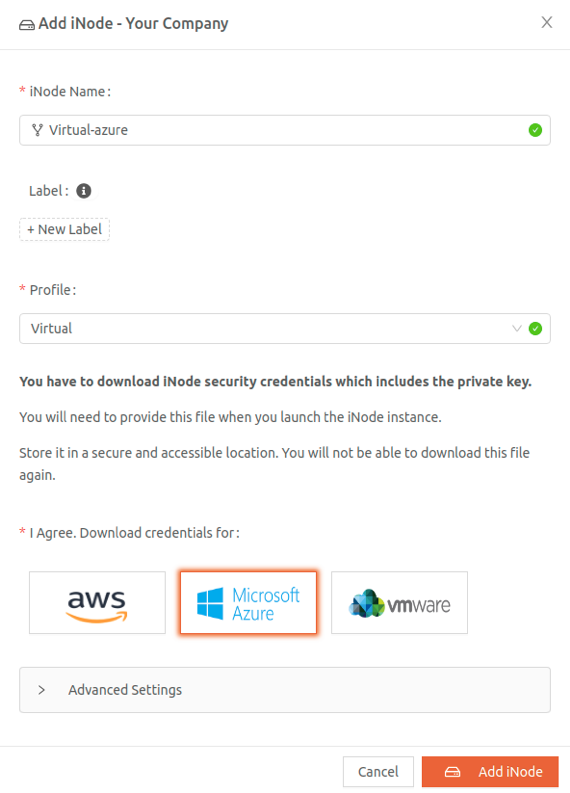
- In the Secure Edge Portal left menu, select the plus icon (+) to display Add iNode.
- Enter the new iNode name.
- Optionally, you can also specify custom attributes as Label. (For more on labels, see Using Labels.)
- Select the Virtual profile.
- Download iNode security credentials that you’ll need when you launch the Virtual iNode. Select Microsoft Azure and then select Add iNode. Note that you can download this file only once. The file contains secure credentials used by the virtual iNode instance.
- Save the downloaded file in a safe place. Don’t share it.
Launch Virtual iNodes on Azure
To launch Virtual iNodes on Azure, use the Secure Edge Azure iNode Launcher, a tool that deploys Secure Edge iNode instances automatically in your Azure subscriptions. It uses your Azure login credentials and associated Azure privileges to copy, build, and deploy iNode VHD files from Secure Edge upstream servers.
To get started, download the Secure Edge Azure iNode Launcher. Follow these steps:
- Log in to the Secure Edge Portal.
- From the bottom of the Dashboard left navigation menu, select the Download Software icon.
- From the Download Software page, select the launcher executable.
Before you run the launcher, make sure you’ve set up your Windows environment with the tools you need to run it successfully, described in the next section.
Prerequisites
The launcher uses Windows built-in components to avoid use of any third-party tools or applications from sources other than Microsoft. You’ll need the following built-in or add-on tools from Microsoft to run the launcher successfully:
- Administrator access to the computer
- Windows PowerShell 5
- Azure PowerShell 5.1
- Windows 10 Pro or Windows Server 2016
- Connectivity to your Azure subscription from the computer
- Azure privileges and sufficient CPU resources to create and modify Azure:
- Create, copy, modify Azure blob storage account
- Access existing Azure resources and create new resources
- Create VM images
- Create virtual machines
- Create and modify networking components such as network security groups (NSG), IP address, network cards, subnets, etc.
If you’re unsure about CPU resources or permissions, please consult with your administrator or Azure support.
You can find the version of Windows PowerShell installed on your computer by running the following cmdlet in the Windows PowerShell window:
$PSVersionTableThe output should be similar to the following:
Name Value ---- ----- PSVersion 5.1.18362.145 PSEdition Desktop PSCompatibleVersions {1.0, 2.0, 3.0, 4.0...}
BuildVersion 10.0.18362.145 CLRVersion 4.0.30319.42000 WSManStackVersion 3.0
PSRemotingProtocolVersion 2.3
SerializationVersion 1.1.0.1You can find out whether Azure PowerShell is installed on your computer by running following cmdlet in the Windows PowerShell window:
Get-Module -ListAvailable | ?{$_.Name -like "Azure*"}The output of the cmdlet should appear as follows:
ModuleType Version Name ExportedCommands ---------- ------- ---- ---------------- Script 0.5.4 Azure.AnalysisServices {Add-AzureAnalysisServicesAccount, Restart-AzureAnalysisSe... Script 4.6.1 Azure.Storage {Get-AzureStorageTable, New-AzureStorageTableSASToken, New... Script 6.13.1 AzureRM Script 0.6.14 AzureRM.AnalysisServices {Resume-AzureRmAnalysisServicesServer, Suspend-AzureRmAnal...
.
.
.If your computer doesn’t have the necessary Azure PowerShell modules installed, run the following commands within the PowerShell window. You must have Administrator permission to run these commands.
Install-Module AzureRm Set-ExecutionPolicy UnRestrictedDepending upon your computer security configuration settings, you may be asked additional questions during the installation process. In most cases, you must allow the settings change to proceed.
Before you start the launcher, you need to rename the Virtual iNode security credentials file you downloaded in Provision a Virtual iNode on Azure. Your iNode security credentials file has the name of your Virtual iNode without any file extension. The launcher requires the file extension to be .yaml. Use the Windows Command shell command rename to add the .yaml file extension to your iNode security credentials file. For example:
rename MyVirtualiNode MyVirtualiNode.yamlRun the Launcher
Once the prerequisites are in place, follow these steps to start the launcher:
- Double click on the launcher executable file.
- When the launcher interface displays, select the Login button to display a window requesting login to your Azure subscription.
- Login to your Azure subscription.
You can use the Secure Edge Azure iNode Launcher for either of these scenarios:
- Fresh Deployment â Used for deploying a new iNode in a new Azure resource group
- Existing Deployment â Used for deploying a new iNode in an existing Azure resource group
Launch a Fresh Deployment
The Fresh Deployment automates the entire deployment process by creating the following Azure resources:
- Azure storage account
- Virtual machine image
- Virtual machine
- Subnet
- Network Security Group
- Network Interface
- Public IP Address
- Port 22 Inbound, 443 Inbound and Outbound NSG rules
To launch a fresh deployment, follow these steps:
- In the launcher, specify the following mandatory fields:
- Azure Subscription - You can select your Azure subscription ID from this dropdown. You see only subscriptions that have privileges assigned to the user account you used to login to your Azure subscription.
- iNode VHD - The latest released version of the iNode is selected for you.
- iNode Security Credentials - This is the Virtual iNode’s security credentials file you downloaded in Provision a Virtual iNode on Azure and renamed to add .yaml file extension.
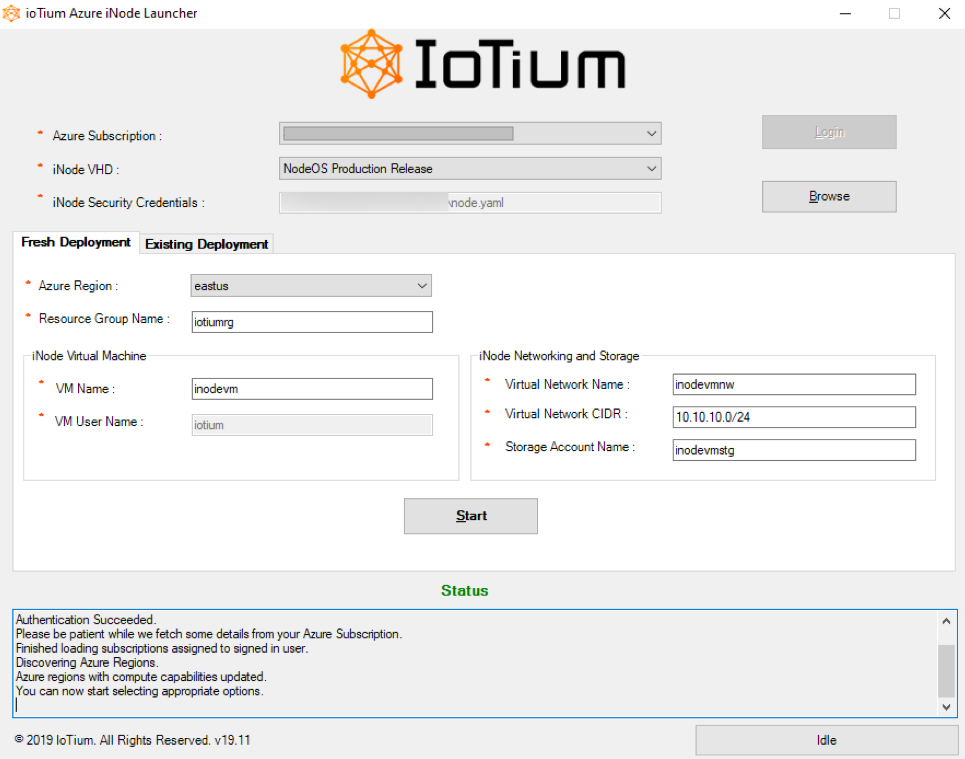
- Select the Fresh Deployment tab and complete the mandatory fields. Note that in the Azure Region field, only the Azure regions that have compute capabilities are displayed.
- Select Start. It takes about 10 minutes to finish.
- If the deployment completes successfully, a success dialog box is displayed. When you select OK, the launcher exits.
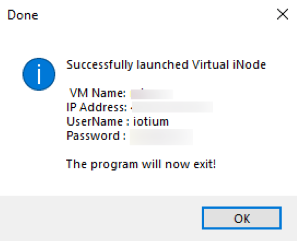
If the deployment fails, a failure dialog box is displayed. When you select OK, the launcher exits. See Log Files for Troubleshooting for help with identifying the why the launch failed.
Launch an Existing Deployment
To launch an existing deployment, follow these steps:
- In the launcher, specify the following mandatory fields:
- Azure Subscription - You can select your Azure subscription ID from this dropdown. You see only subscriptions that have privileges assigned to the user account you used to login to your Azure subscription.
- iNode VHD - The latest released version of the iNode is selected for you.
- iNode Security Credentials - This is the Virtual iNode’s security credentials file you downloaded in Provision a Virtual iNode on Azure and renamed to add .yaml file extension.

- Select the Existing Deployment tab to deploy the new iNode in an existing Azure resource group.
- Select your Azure region (only the Azure regions that have compute capabilities are displayed) and resource group. All fields under the Existing Deployment tab except VM Name are retrieved from the selected region and resource group. Fill in the iNode VM name. Be sure that the name you choose doesn’t contain any characters that aren’t supported for Azure filenames (!@#$%^&*)
- For the iNode image, you can either download the latest iNode image from Secure Edge upstream servers or use an existing iNode image created earlier.
- To download and use the latest iNode image, leave the field iNode Image Name unselected.
- To use an existing iNode image in the selected resource group, select the existing image in the iNode Image Name field.
If you select the Start button with the iNode Image Name field unselected, you’ll be prompted with the following dialog: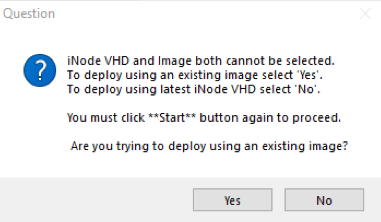
Select Yes or No:
Yes - Download the latest iNode VHD from Secure Edge upstream servers.
No - If you select no, go back and select an existing image in your resource group. This doesn’t download anything from Secure Edge upstream servers and uses an existing VM image created earlier. You must have deployed at least one image using the Launcher to be able to select the image name from the list.
- Select Start. It takes about 10 minutes to finish.
- If the deployment completes successfully, a success dialog box is displayed. When you select OK, the launcher exits.

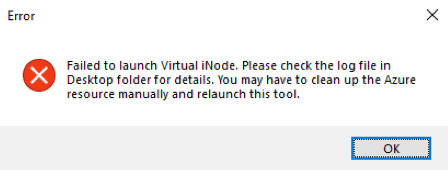
If the deployment fails, a failure dialog box is displayed. When you select OK, the launcher exits. See Log Files for Troubleshooting for help with identifying the why the launch failed.
Log Files for Troubleshooting
The launcher places two log files on the logged in user’s desktop or the user profile that is used to run the launcher. These can be used for troubleshooting.
- Secure Edge.Az.csv - Contains the operations logs from the Azure subscription. If you operate in a strict or role-based access control environment, you may not be able to see this file.
- Secure Edge.UI.log - Contains the PowerShell transcript information. Logs in this file may be used to identify operations failure.
Provisioning and Launching Virtual Edge iNodes with Azure
This section describes how to provision and launch Virtual Edge iNodes with Azure.
Provision a Virtual Edge iNode on Azure
To provision a Virtual Edge iNode with Azure, follow these steps:
- In the Secure Edge Portal left menu, select the plus icon (+) to display Add iNode.
- Enter the iNode name.
- Optionally, you can also specify custom attributes as Label. (For more on labels, see Using Labels.)
- Select the Virtual Edge profile.
- Download iNode security credentials that you’ll need when you launch the Virtual Edge iNode. Select Microsoft Azure and then select Add iNode. Note that you can download this file only once. The file contains secure credentials used by the virtual Edge iNode instance.
- Save the downloaded file in a safe place. Don’t share it.

Launch Virtual Edge iNodes on Azure
To launch Virtual Edge iNodes, you need to be logged in to your Azure account with your Azure credentials. Once you’re logged in, the launch process includes the following tasks:
- Create the resource group, storage account, and container blob
- Copy an Azure-ready Virtual Hard Disk (VHD) from Secure Edge
- Create an image from the ioTium VHD file
- Create a virtual network, network interface, and public IP address
- Launch the Virtual Edge iNode virtual machine (VM)
- Add a route to the route table and associate it with the virtual network
The following sections describe these steps in detail primarily using the Azure Portal, but you can also use the Azure CLI or any other Azure-capable application programming interface (API) .
Refer to naming rules and restrictions for Azure resources. In particular, avoid using special characters in the container name.
Create the resource group
If you don't plan to use an existing resource group, you'll need to create one.
- In the Microsoft Azure portal, select Resource groups.
- Select Create to create a new group.
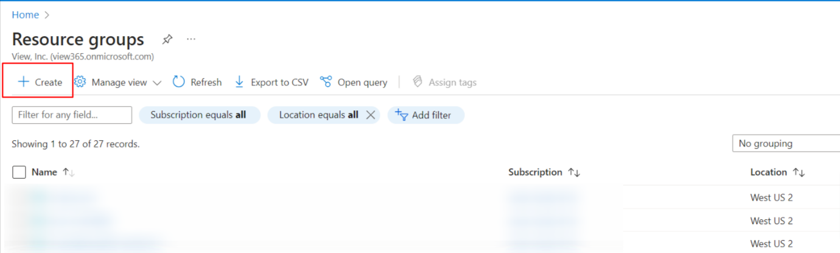
- Name the resource group, select the region where the Virtual Edge iNode should be created, and then select Review + create.
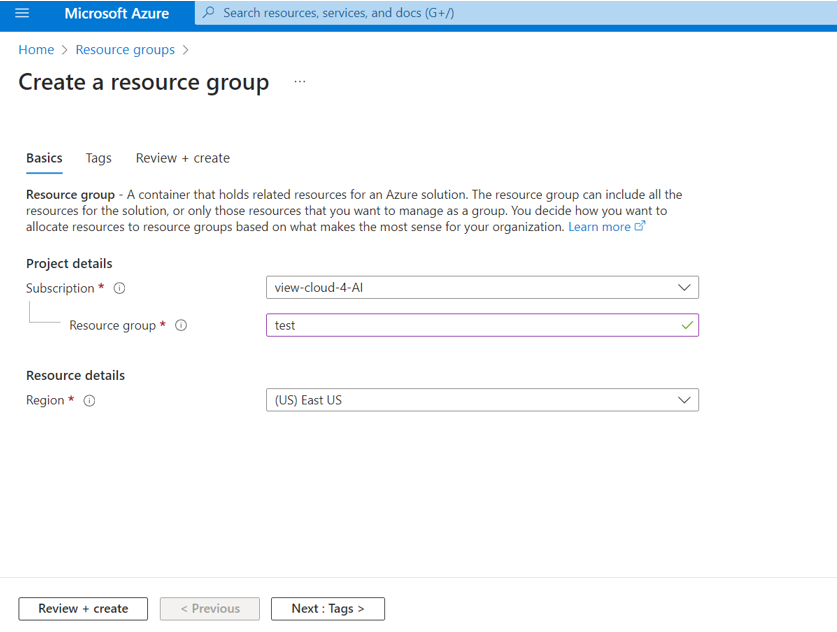
- Refresh the page and verify that the resource group has been created.
Create the storage account and container
- In the Azure Portal, select Storage accounts.
- Select the storage account where the VHD file will be uploaded. If you don’t have a storage account, select + Create to create one.
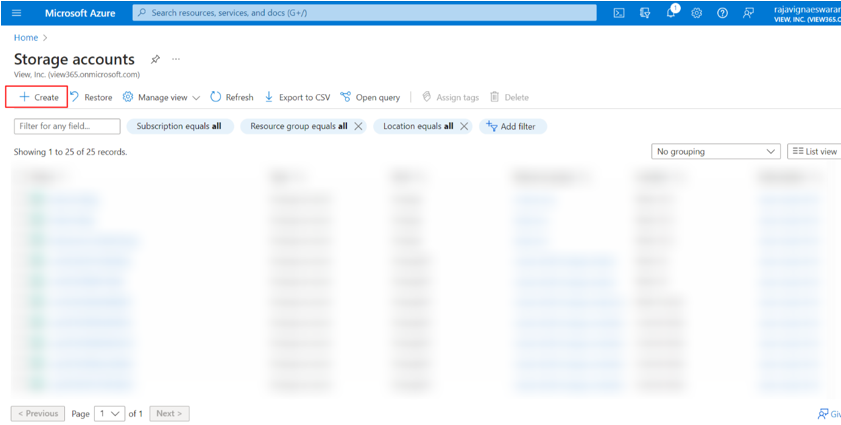
- Give the storage account a name, select Performance as Premium and select the same Resource group that you selected or created in Create the resource group. Select the same region for the storage account that you selected for the resource group.
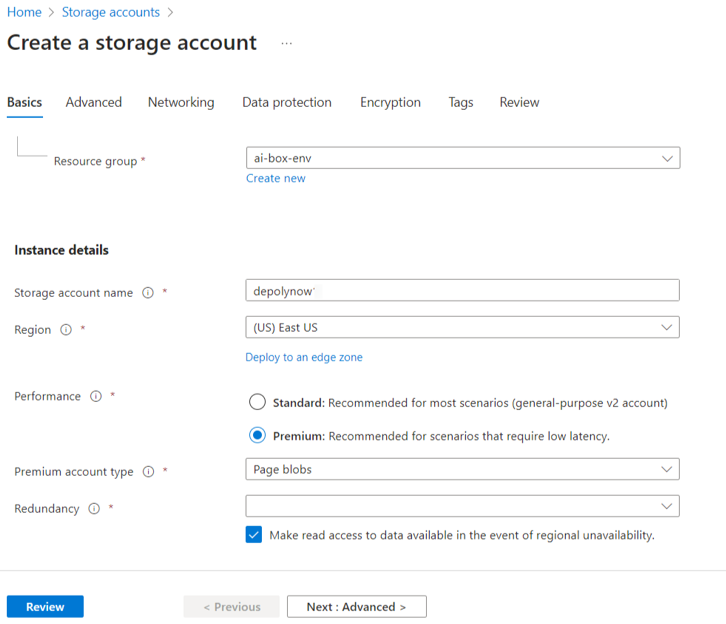
- Refresh the page and verify that the storage account was created.
- In the storage account under Blob service, select Containers.
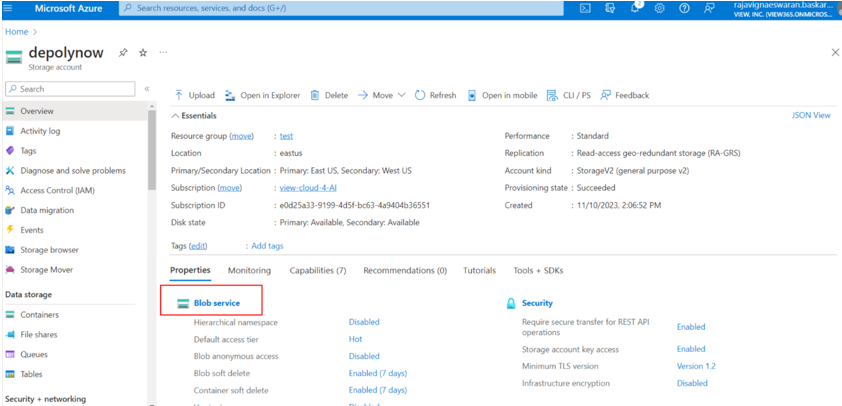
- Select a container to use to upload the Azure-ready VHD file. Or, if you don't have a storage container, select + Container to create one.
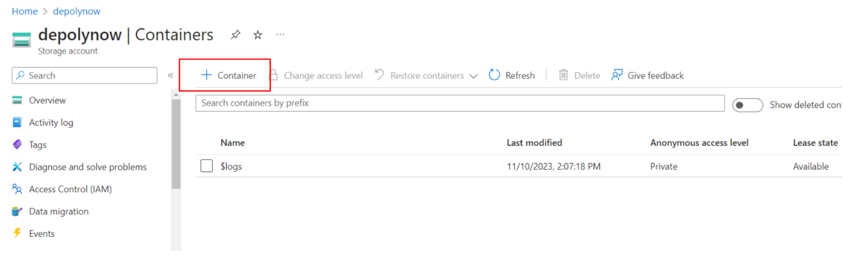
- Enter a name for the new storage container and select Create.
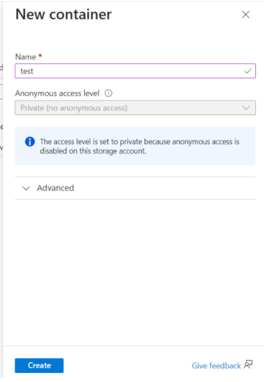
- Refresh the page and verify that the container was created.
Copy the Azure-ready VHD file from Secure Edge
You need to copy the Azure-ready VHD file to launch the Virtual Edge iNode in Azure. We recommend that you copy the VHD file using the Azure CLI because this method is faster. You can also use the Azure portal or any other Azure-capable API to complete the following steps.
- From the top navigation of the Azure portal, select the Cloud Shell icon to open a Bash shell.
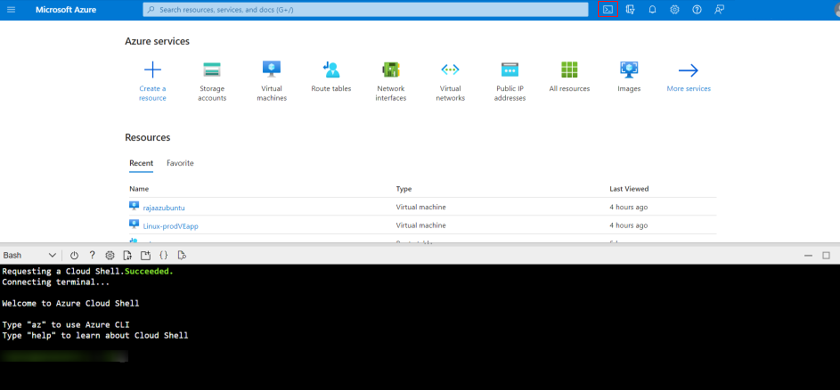 The first time you open a Bash shell, Azure creates a storage name that it associates with the storage account you created previously. This is used to save the configuration files (custom-data.txt) used for deploying a Virtual Edge iNode. After you open the Bash shell the first time, any subsequent times that you select the Azure CLI the Bash shell will open automatically.NoteWe don’t use the storage name created by Azure during the configuration. Nonetheless, don’t remove it. Azure associates the storage name with the console; if it’s removed, the configuration files will not be available.
The first time you open a Bash shell, Azure creates a storage name that it associates with the storage account you created previously. This is used to save the configuration files (custom-data.txt) used for deploying a Virtual Edge iNode. After you open the Bash shell the first time, any subsequent times that you select the Azure CLI the Bash shell will open automatically.NoteWe don’t use the storage name created by Azure during the configuration. Nonetheless, don’t remove it. Azure associates the storage name with the console; if it’s removed, the configuration files will not be available. - Use the following CLI command to copy the VHD file, replacing the variables with the correct names for your account, container, destination, and VHD file:Shell
az storage blob copy start --account-name <MyStorageAccName> --destination-container <MyContainerName> --destination-blob <IoTiumVHDFileName> --source-uri
In the following example, the command copies the VHD file named nodeos-production.vhd from the link https://iotiumstore.blob.core.windows.net/release/latest/nodeos-production.vhd to a local container test in a storage account depolynow.
az storage blob copy start --account-name depolynow --destination-container test --destination-blob nodeos-production.vhd --source-uri
https://iotiumstore.blob.core.windows.net/release/latest/nodeos-production.vhdOn executing the above command, the blob for the VHD file is created in the container, allocating 11.2 GB immediately. Then it starts copying the VHD file, which might take a long time depending on network connection and the location of the Azure storage account.
The copied VHD file is available in the container as blob.
Create an image using the ioTium VHD
- In the Azure portal, select Images and then select + Create.
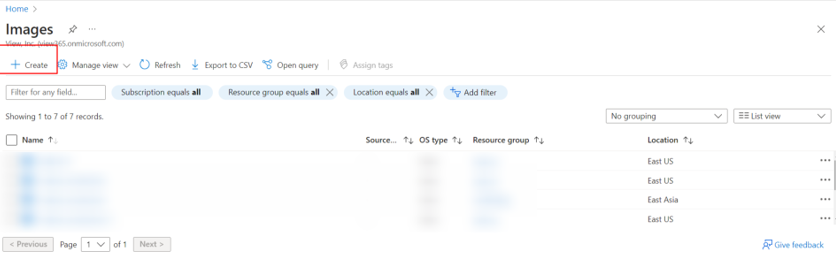
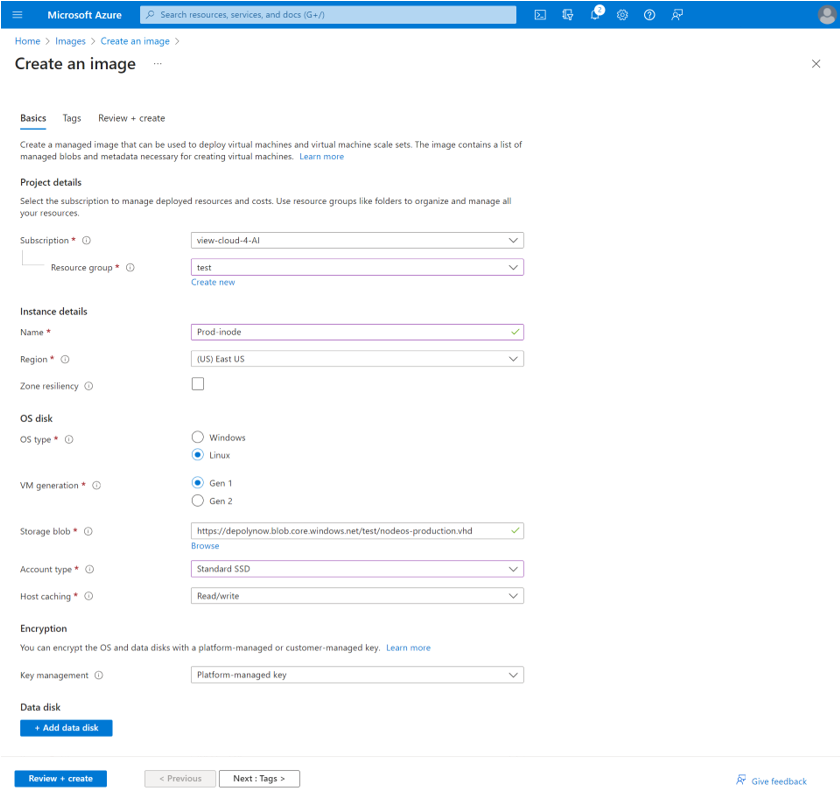
- Complete the fields as follows:
- Give the image a name. Remember that this image is a template that will later be deployed to a Virtual Edge iNode with a different name.
- Ensure that the region is the same as the region of your storage account
- Set OS type to Linux.
- In the Storage blob field, select Browse to open a panel that lists your storage accounts. Navigate through the storage accounts and containers to locate the VHD that you copied.
- Set Account Type to Standard SSD.
- Select Review + create and review the image creation details.
- Select Create to complete the image creation.
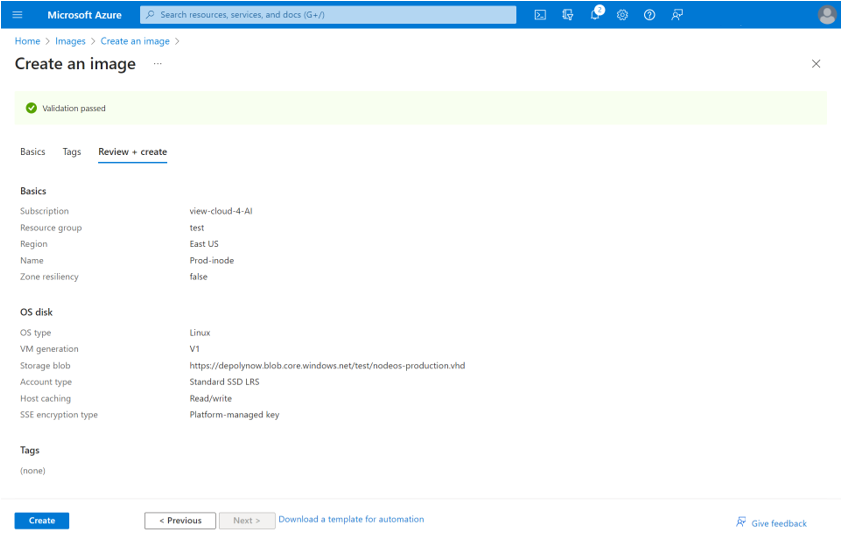
- When the process is completed, return to the Images panel and verify the new image was created. You can now use this new image to deploy the Virtual Edge iNode in Azure.
Create the virtual network and network interface
The virtual network is your cloud subnet for your application instance and Virtual Edge iNode instance
- In the Azure portal, select Virtual Network. If you don’t have a virtual network, select + Create to create one.
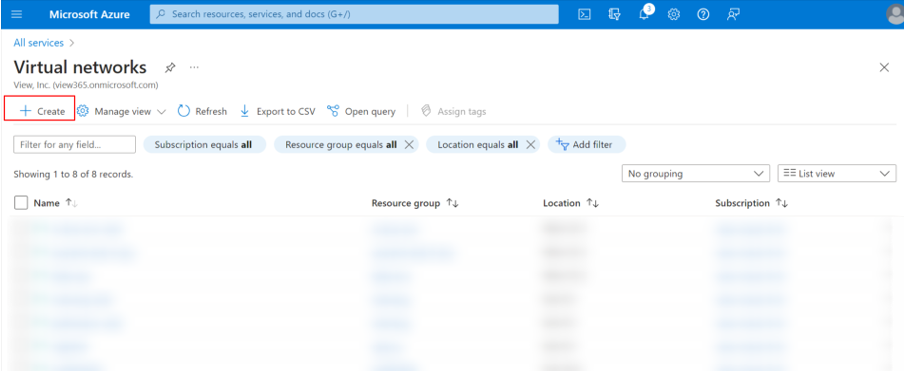
- Give the virtual network a name and choose the region that is the same as the storage account and resource group.
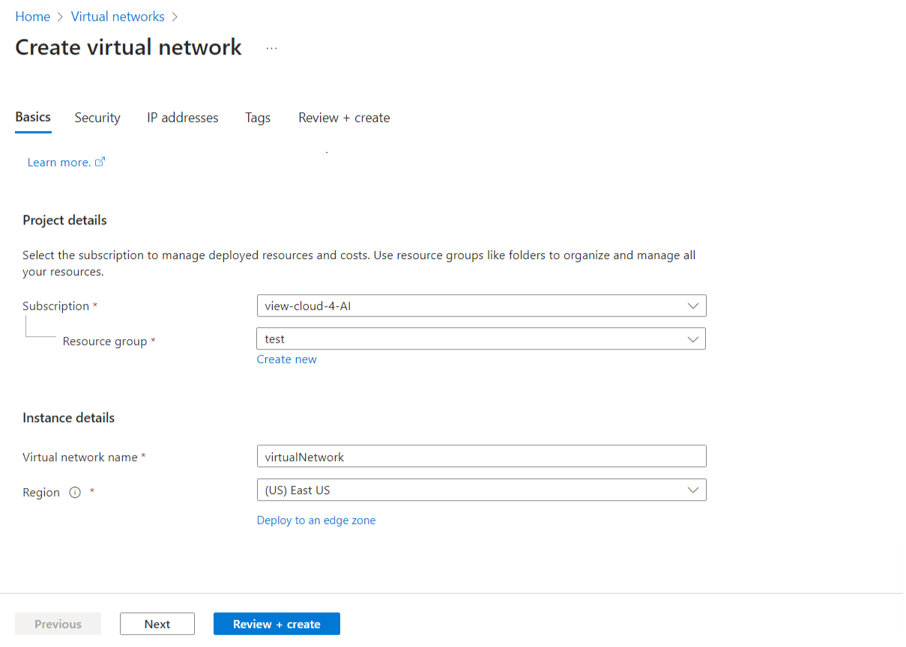
- In the IP Addresses tab, create two subnets. First, add a subnet with a name and address range in the virtual network. This typically takes a few minutes to complete.
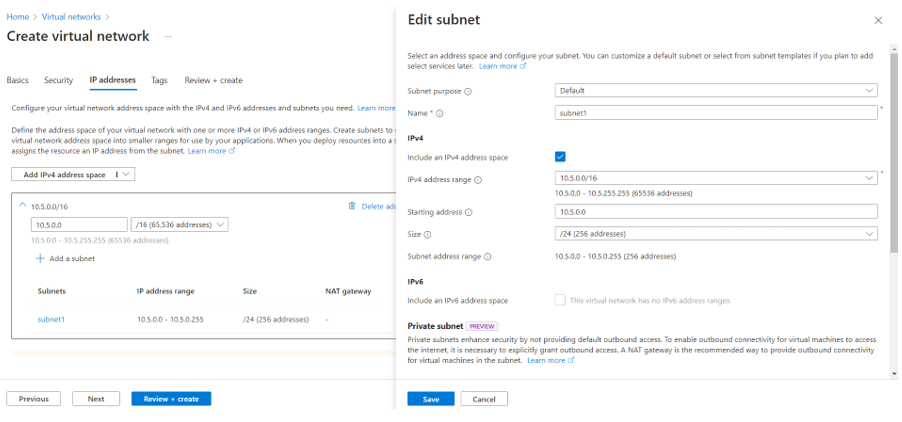
- Then, add one more subnet in the same virtual network.
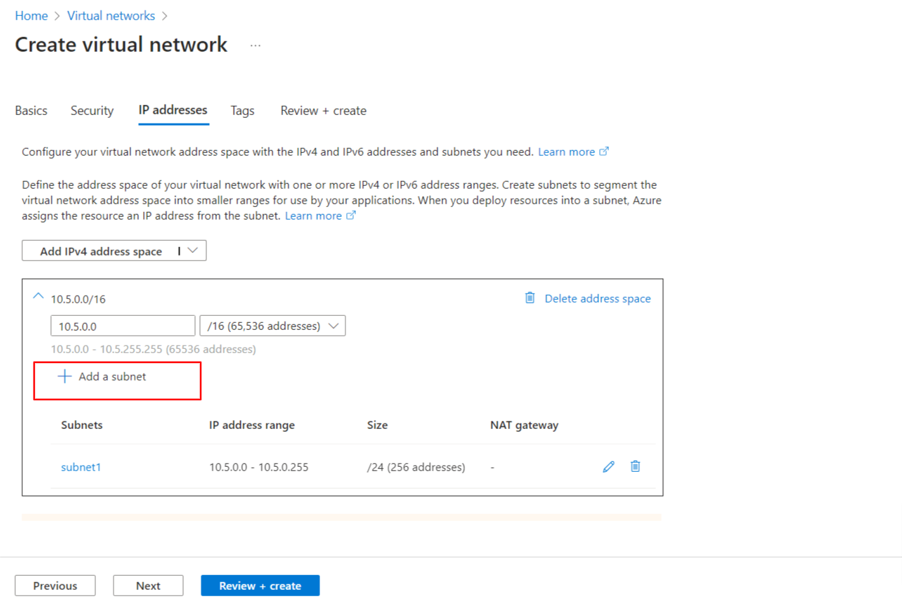
- The Virtual Edge iNode needs two network interfaces to communicate with other devices in the virtual network. Select Network Interface > Create.
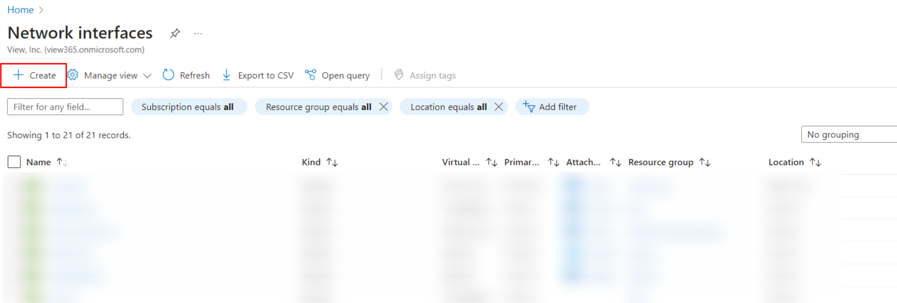
- Under Subnet, select the subnet created in Step 3, the same region as the resource group and storage account, and then select Create. This interface will be Internet facing and will take a few minutes to create.
- Repeat Steps 5 and 6 to create one more network interface to map to the TAN network.
Create a public IP address
The Virtual Edge iNode needs a public IP address to communicate with the Edge iNode and the Secure Edge portal.
- In the Azure portal, select Public IP address > Create.
.png)
- Select IPv4 for IP version, Dynamic for IP address assignment, and select the resource group and region.
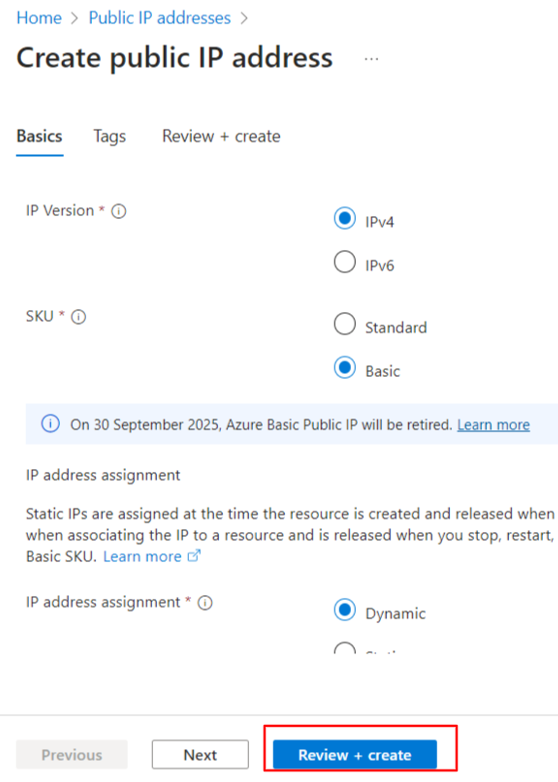
- Now, you'll need to apply the public IP address to the network interface created in the previous section. On the public IP address, select Associate and in teh Associate pubic IP address window, select resource type Network Interface and select the interface from the drop-down list.
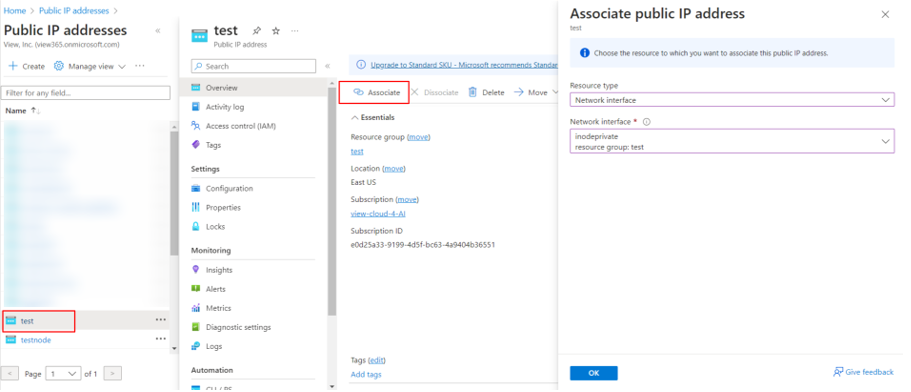
- Select OK to apply the configuration.
Launch the Virtual Edge iNode VM
Launch the Virtual Edge iNode VM in the same resource group and region where you created the image and network interface. The following steps use the Azure CLI for simplicity, however you can also use the Azure Portal or any other Azure-capable API to complete these steps.
- You should have a file containing Virtual Edge iNode security credentials that you downloaded in Provision a Virtual Edge iNode on Azure. Open that file and copy its contents.
- Open the Bash (Linux) Azure Cloud Shell.
- In the Azure Bash shell, type the following command to open a new file custom-data.txt:Shell
vi custom-data.txt - Paste the contents of the iNode credentials file you copied in Step 1 into this file and save your changes.
- Finally, launch the Virtual Edge iNode instance with the following command:
Below is an example.az vm create -g test --image <image-name> --name <VM name> --custom-data <custom-data name> --nics <network interface 1 name> <network interface 2 name> --size Standard_B2s --admin-username iotium --admin-password "yourpasswordhere"
az vm create -g test --image Prod-inode --name Prod-inodeVE --custom-data custom-data.txt --nics inodeprivate TAN --size Standard_B2s --admin-username iotium --admin-password "examplepassword!"This action typically takes a few minutes to complete. To check whether the Virtual Edge iNode was launched successfully, log in to the Secure Edge Portal and see the iNode status shows as ALIVE.
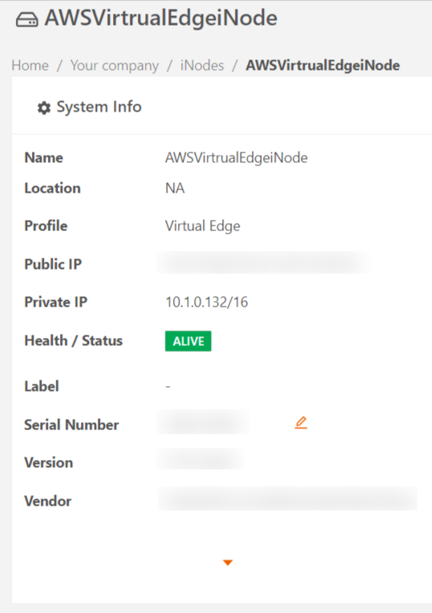
Add a route and associate it with the virtual network
- In the Azure portal, select Route tables and then select Create.
- Assign a name and select the resource group and region you used for the Virtual Edge iNode.
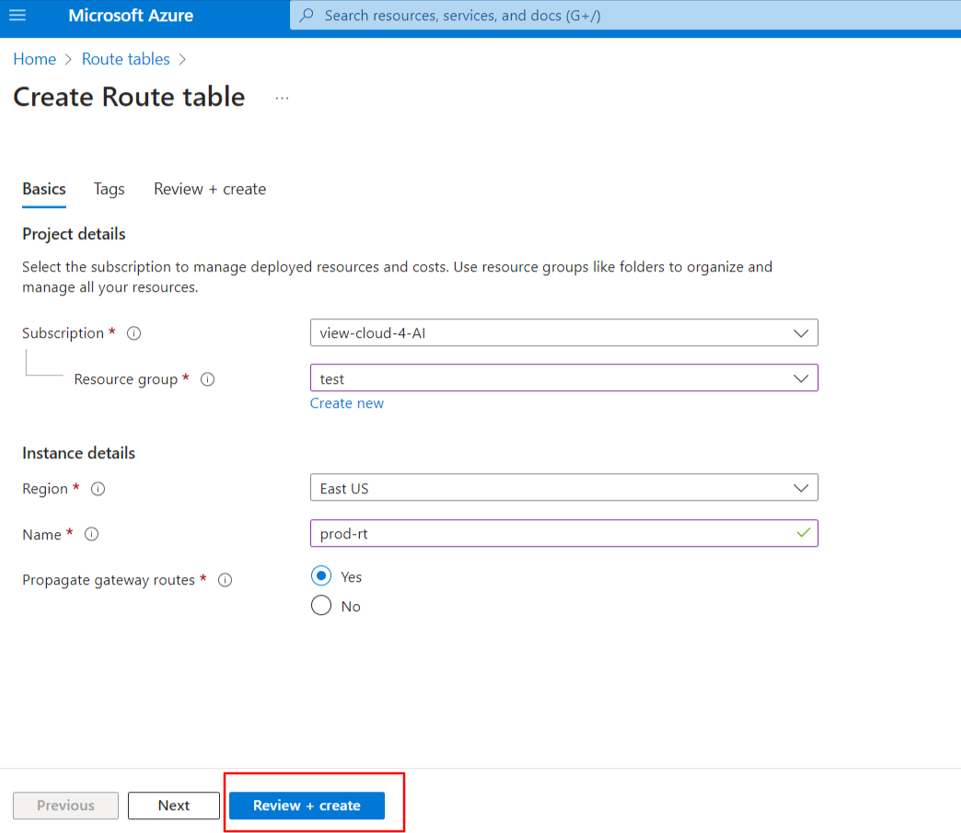
- In the route table, select Select routes and then select Add.
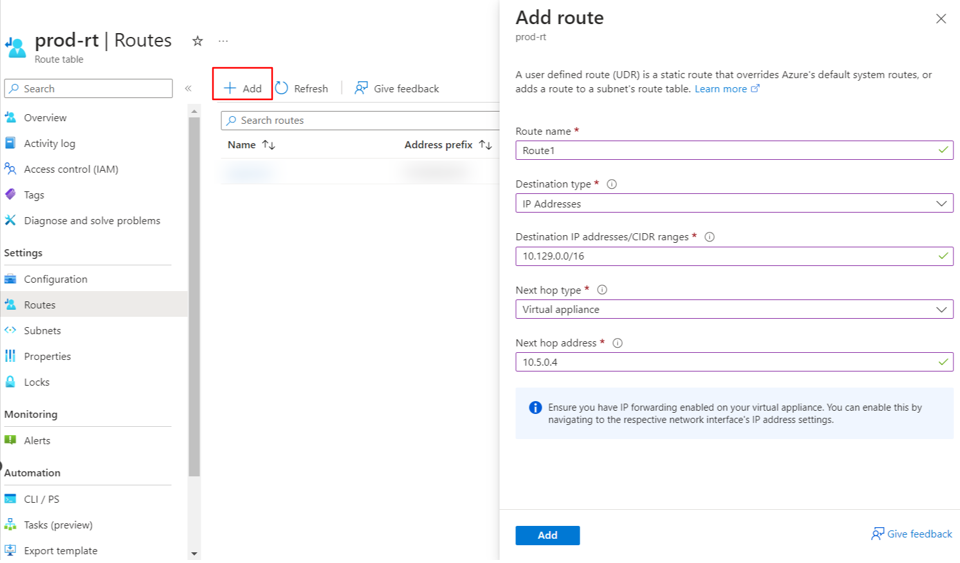
- Name the route and enter the TAN Network Subnet for Address Prefix.
- Set Next hop type as Virtual appliance. Set Next hop address to the private IP address of the Virtual Edge iNode.
- To associate the route to the virtual network, select Route table > Subnets.
- Select Associate and Virtual Network to associate the route to the virtual network.

















 The first time you open a Bash shell, Azure creates a storage name that it associates with the storage account you created previously. This is used to save the configuration files (custom-data.txt) used for deploying a Virtual Edge iNode. After you open the Bash shell the first time, any subsequent times that you select the Azure CLI the Bash shell will open automatically.
The first time you open a Bash shell, Azure creates a storage name that it associates with the storage account you created previously. This is used to save the configuration files (custom-data.txt) used for deploying a Virtual Edge iNode. After you open the Bash shell the first time, any subsequent times that you select the Azure CLI the Bash shell will open automatically.







.png)



